Trending Phish and Security Threats

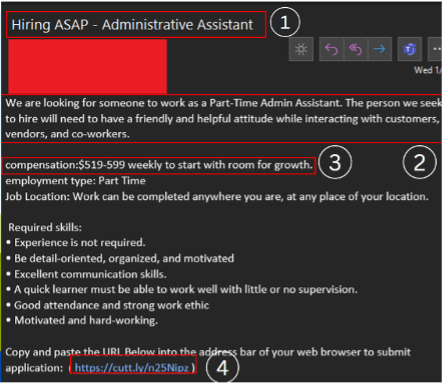
Did you get it all?????
Here are some reasons these mails are tagged phishing mail and how to find them:
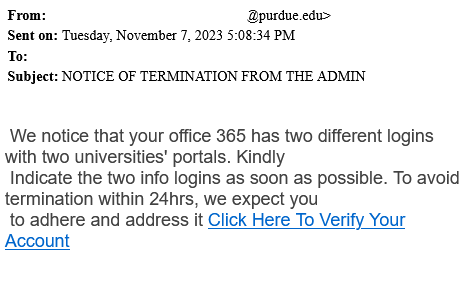
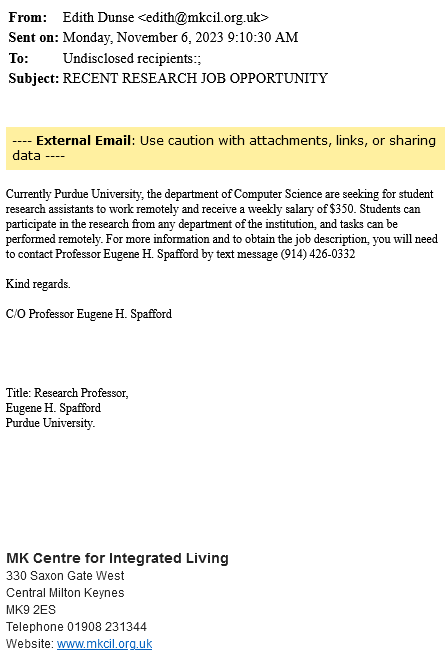
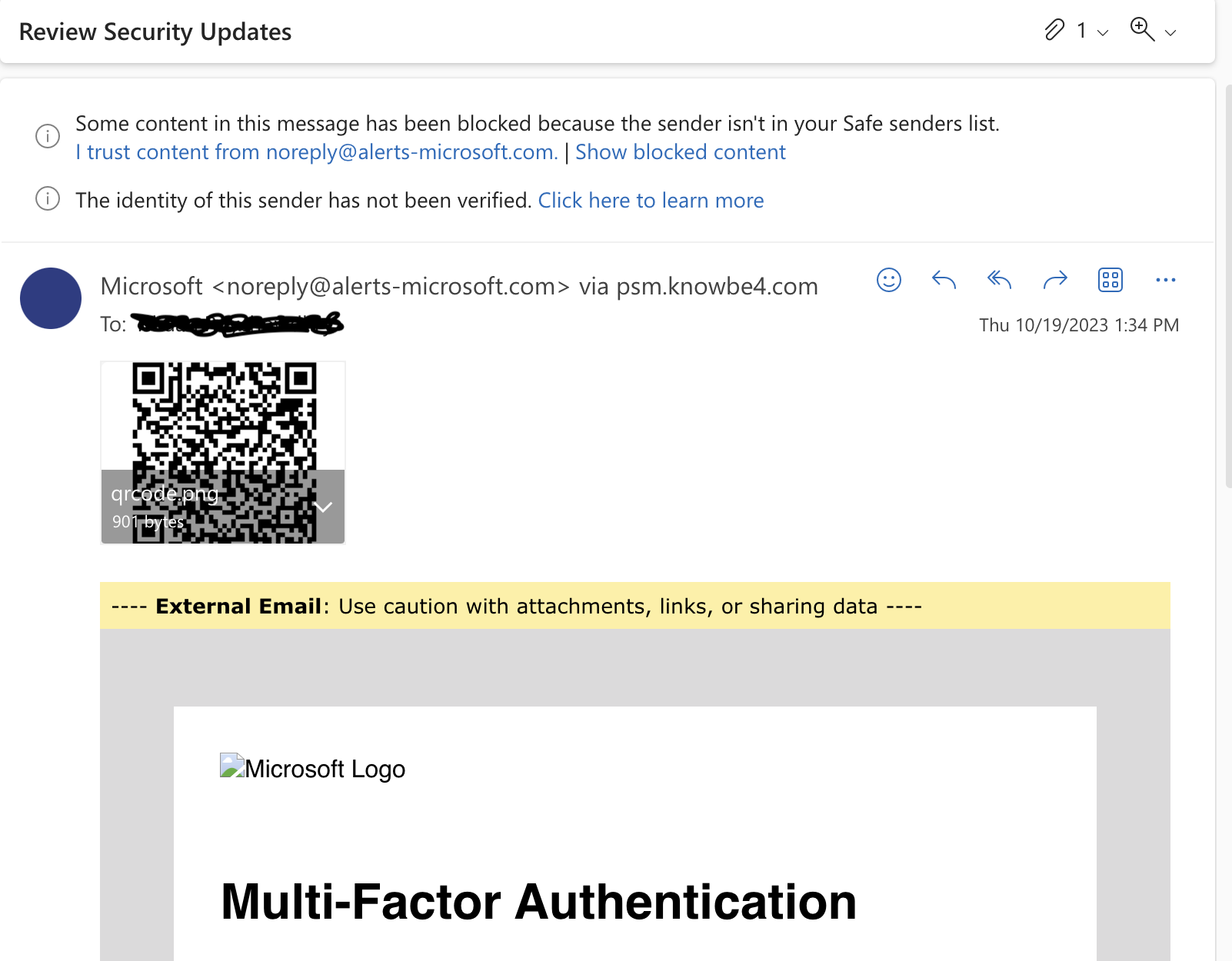
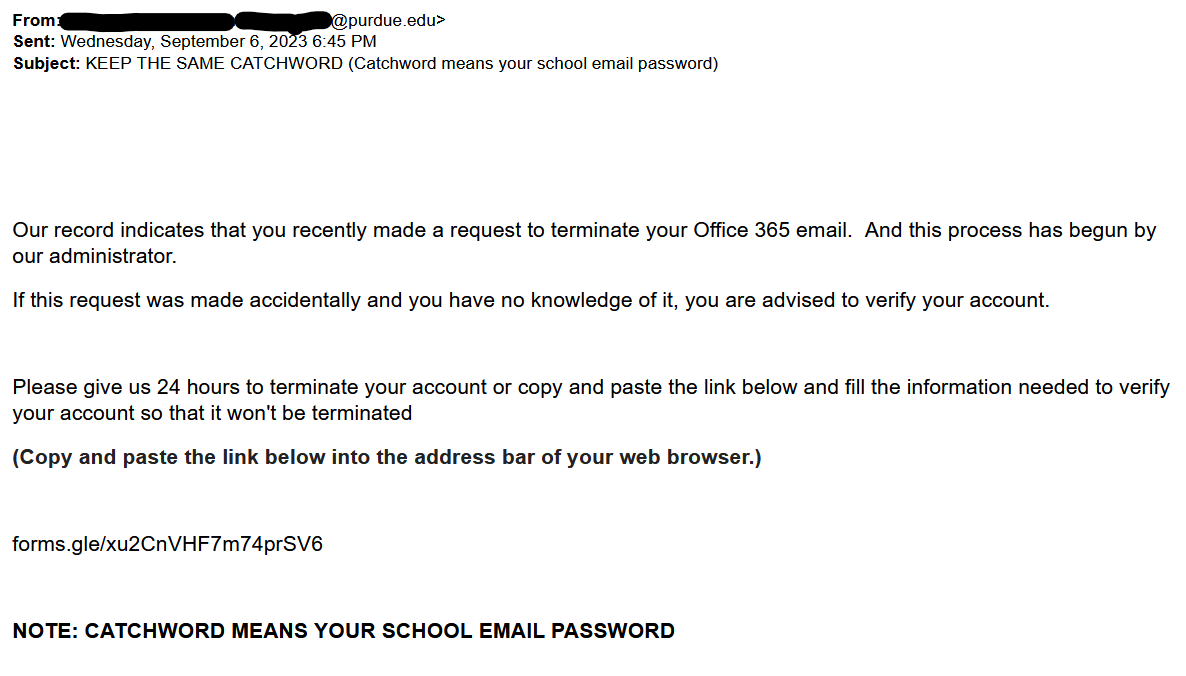
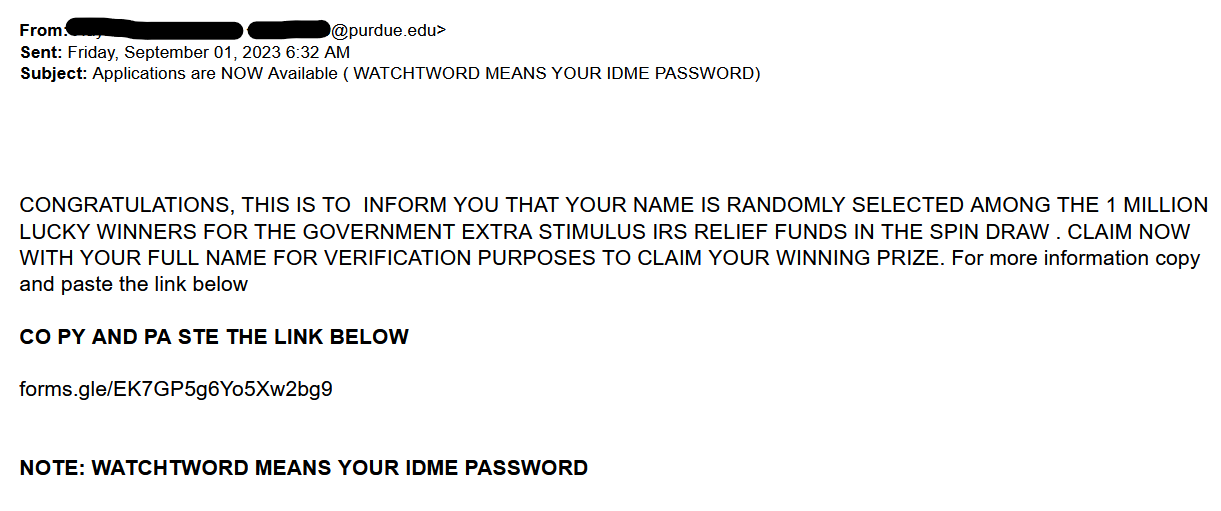
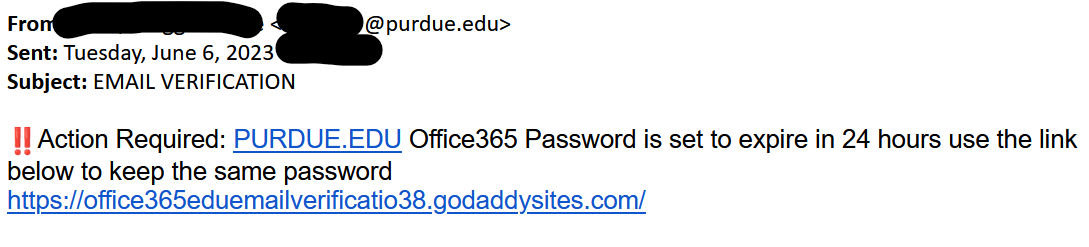
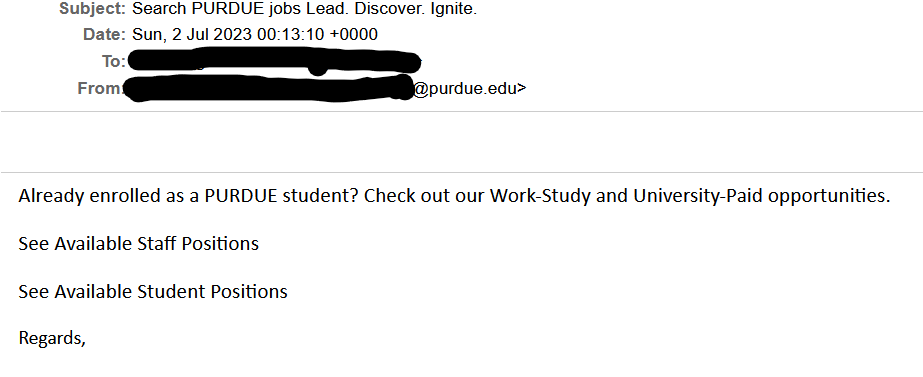
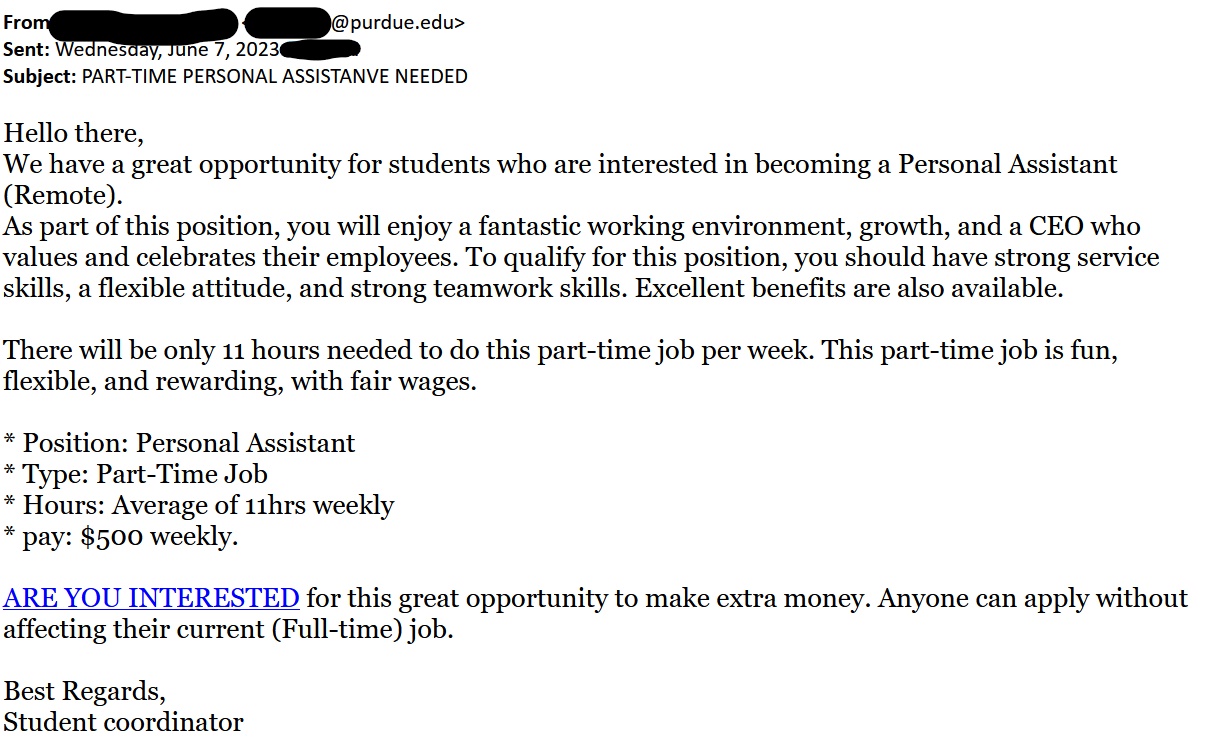
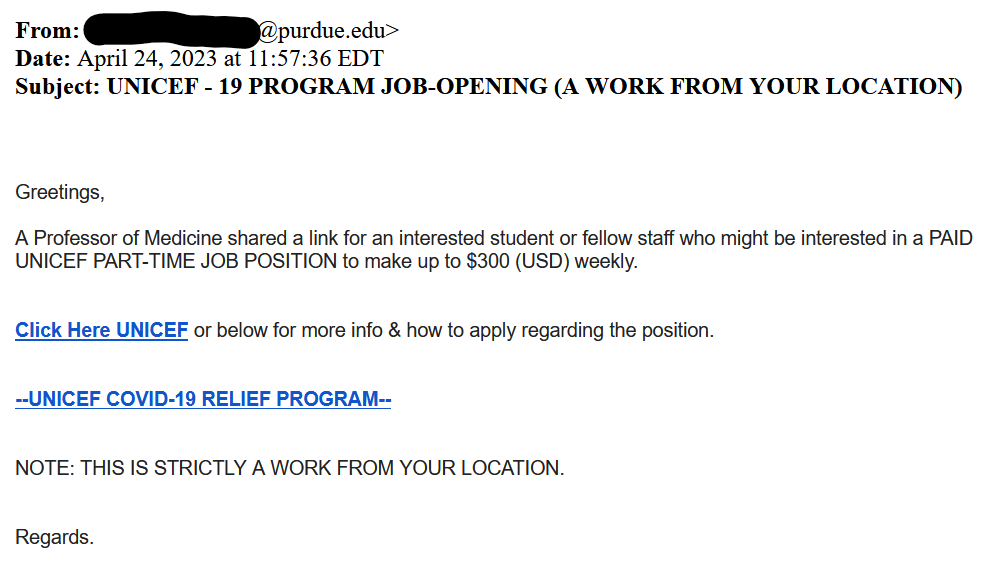
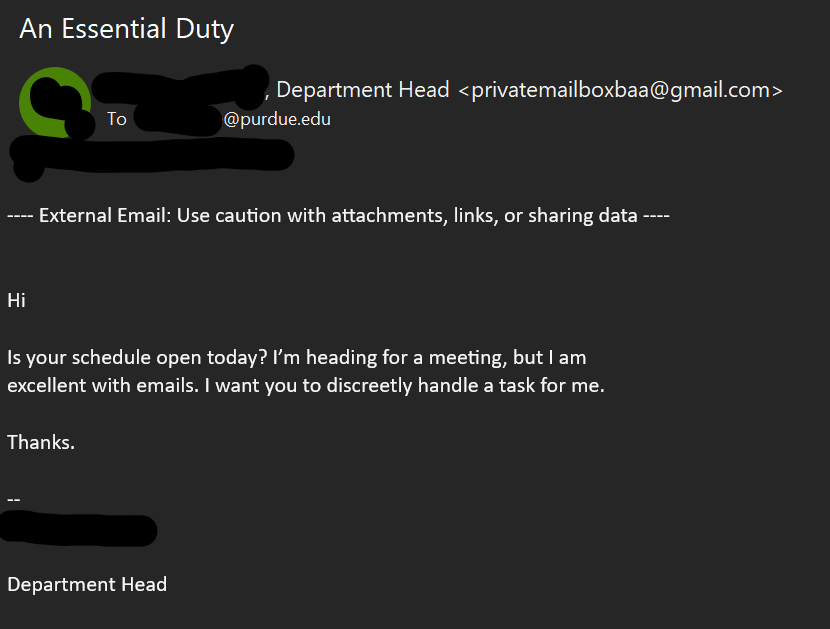
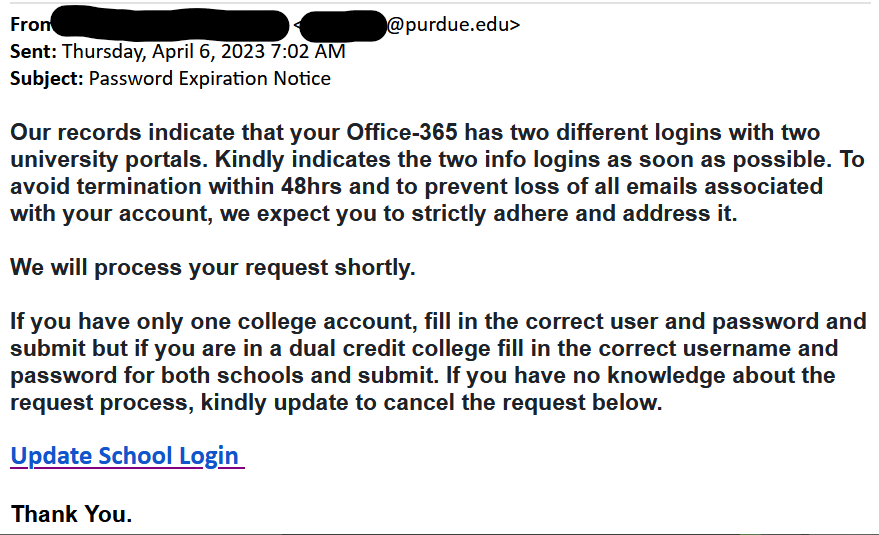
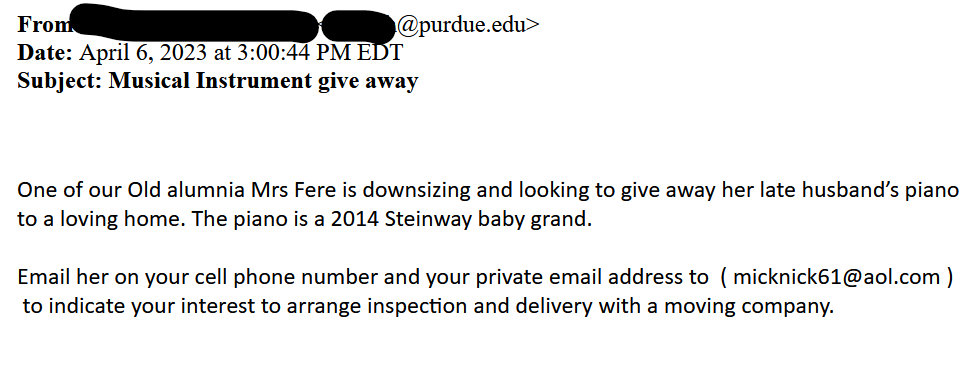
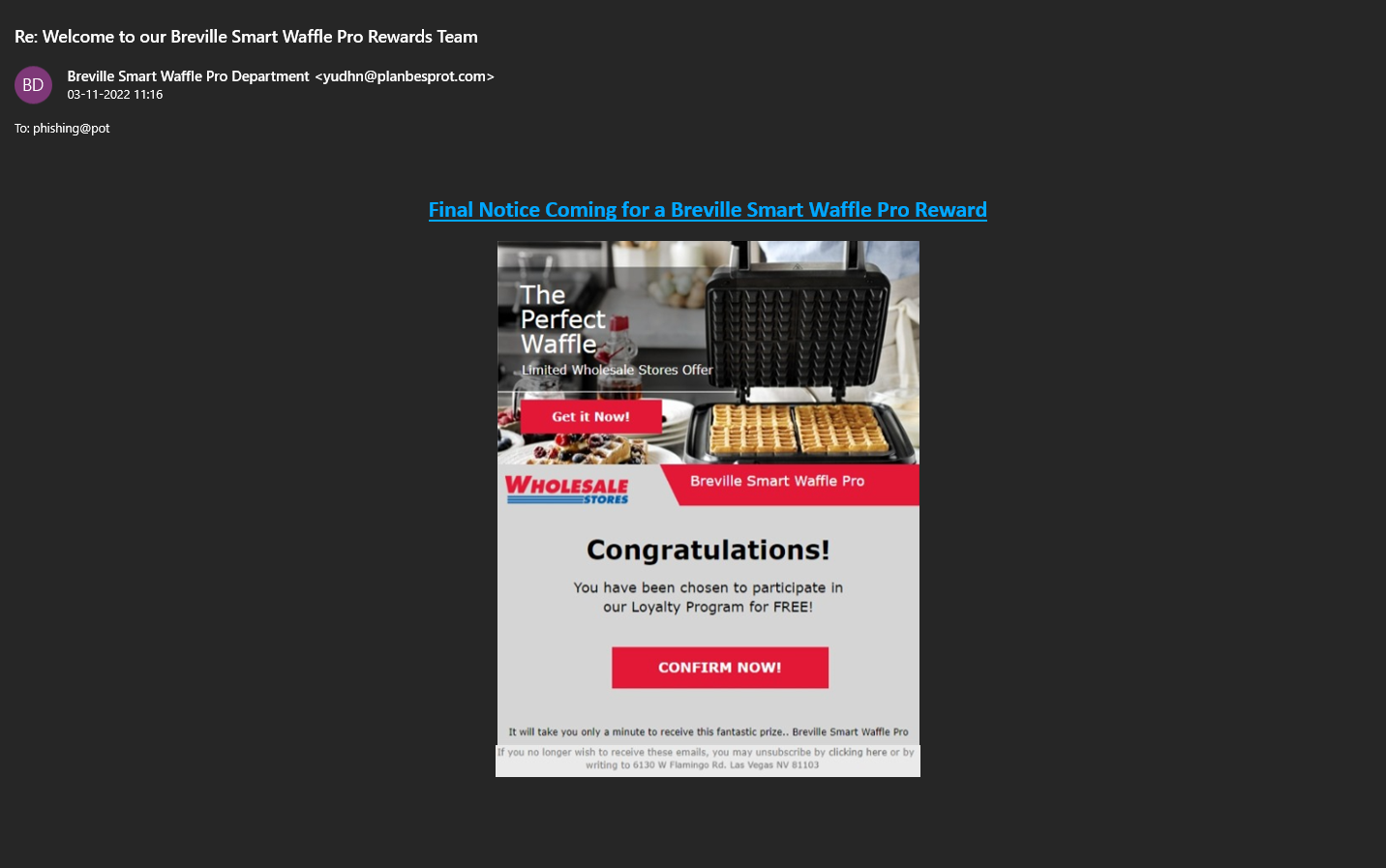
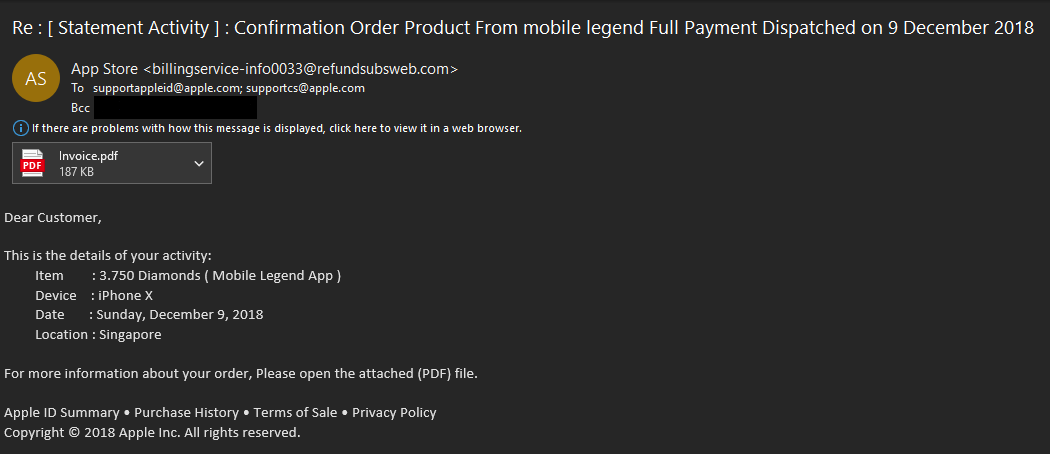
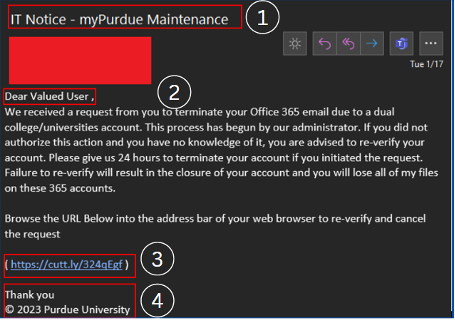
- The First thing to check in any mail is “Is it from a valid source?” Is the sender has a valid user ID from Microsoft or from “ITAP” if not, then it is better we be aware of this sort of mails
- The next thing is any mail from Microsoft will not start with “Dear Valued user” as it will be directly addressed to you.
- The link address would have a Microsoft address, not a form created by a third-party application. So always verify the address of a link before you click it. And even if we are clicking the link never disclose any sensitive personal information like username, phone number, E-mail ID, or password.
- The copyright from the university will always be a logo and will be unique to the university. If the signature looks suspicious, we can conclude that this could be phishing mail.
Finally, all phishing emails are created in a way to risk a sense of panic or urgency so that we might act on impulse. So never panic about the false emails and reach out to us on:
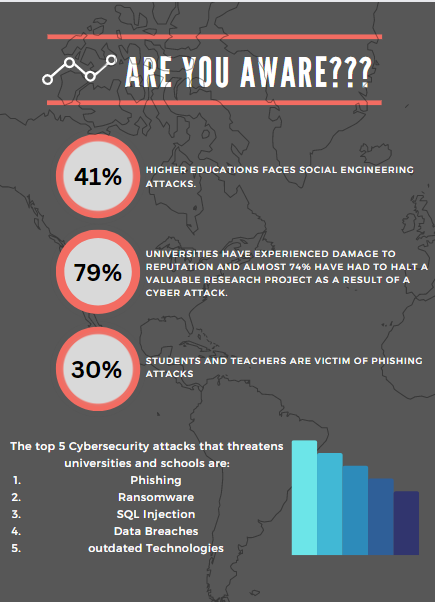
Over the world, all researchers and cybersecurity professionals work on preventing cyber-attacks that risk data and financial loss. Most feel that one of the below is potential causes of an attack:
- Disruption — Reliance on weak and incomplete things that results in compromising the availability of a service to the customers.
- Distortion — The intentional spread of misinformation, which causes trust in information integrity to be compromised.
- Deterioration — Rapid advances in intelligent technologies negatively impact organizations’ ability to control their own information.
With the above in my here is a closer look of potential cyber threats for the year 2023:
1. Exploitation of the smart devices:
At the moment, as AI and machine learning have developed, it has been more completely integrated into smart devices, from lightbulbs and speakers to cars. By 2025, it is predicted that there will be 75.4 billion Internet of Things devices in the world that will be installed and it is no surprise that these smart devices will be considered attack targets for cyberattacks throughout 2023.
Tina Grant, quality assessor at UK-based aerospace company Aerosphere forecasts that cyber-attacks targeting smart devices will predominantly affect autonomous devices with multiple points of attack, for example, smart cars.
Grant says: “Today's automobiles come equipped with automatic features including airbags, power steering, motor timing, door locks, and adaptive cruise control aid systems. These vehicles use Bluetooth and Wi-Fi to connect, which exposes them to a number of security flaws or hacking threats. “With more autonomous vehicles on the road in 2023, it is anticipated that attempts to take control of them or listen in on conversations will increase.
2. Phishing and Social Engineering:
Phishing attacks soared in 2022, with the international consortium and fraud prevention group the Anti-Phishing Working Group recording a total of 3,394,662 phishing attacks in the first three quarters of 2022. There were 1,025,968 attacks in Q1, 1,097,811 attacks in Q2, and 1,270,883 attacks in Q3, with each quarter breaking the record as the worst quarter APWG has ever observed.
Moran general manager of automated prepaid card fraud protection software Arden at financial protection service Brightwell, predicts that eCommerce sites will be hit particularly hard by this, as they are vulnerable to Bank Identifying Number (BIN) attacks which see fraudsters take incomplete card details gained during phishing or social engineering attacks (i.e. the first six numbers of a bank card) and use software to randomly generate the rest of the information needed. The malicious actors will then use e-commerce sites to test whether the details are correct and/or if the cards are active.
3. Cloud Security attacks:
As the global workforce continues to work in an increasingly remote or hybrid capacity, the need for cloud migration has become clear. As companies migrate some or all of their assets to the cloud, the need for cloud security has increased. When surveyed by Cyber Security Hub, one in four (25 percent) of cyber security professionals said that their companies were investing in cloud security capabilities.
With many companies shifting to the cloud, a lot of company data get stored in the cloud which in turn increases the risk of high loss value. For example, even if a company hosts a large amount of valuable customer data, even a partial breach can have far-reaching negative effects. This is because a company’s cloud storage contains “enormous hordes of extraordinarily valuable data”, even if an attacker only gains access to a fraction of this data, they can do real damage with it.
Archived Spam and Phishing Samples: