Guidance Document - VeraCrypt Installation and Use
VeraCrypt Tutorial
Outline
- Installing the Software
- Setting up an encrypted container
- Usage
Installing the Software
The software is free and can be installed by anyone with administrative privileges to the computer on which it is being installed. The host website that was vetted by Purdue's export control office is:
https://archive.codeplex.com/?p=veracrypt
Codeplex.com has been deemed a safe place to download this software, if this site stops hosting the download, please contact the export control office to get an updated download option.
Finally, if you are doing work that requires encryption, whatever machine you are installing it on must be approved by the export control office.
Setting up an encrypted container
-
Open VeraCrypt and click on “Create Volume”

-
Ensure the “Create an encrypted file container” option is selected and click “Next”

This has been established as the most user friendly method to create an encrypted space. With this method, you can create an encrypted file on the approved machine itself, or on any approved external data storage device (i.e. external hard drive with a serial number reported to the export control office)
-
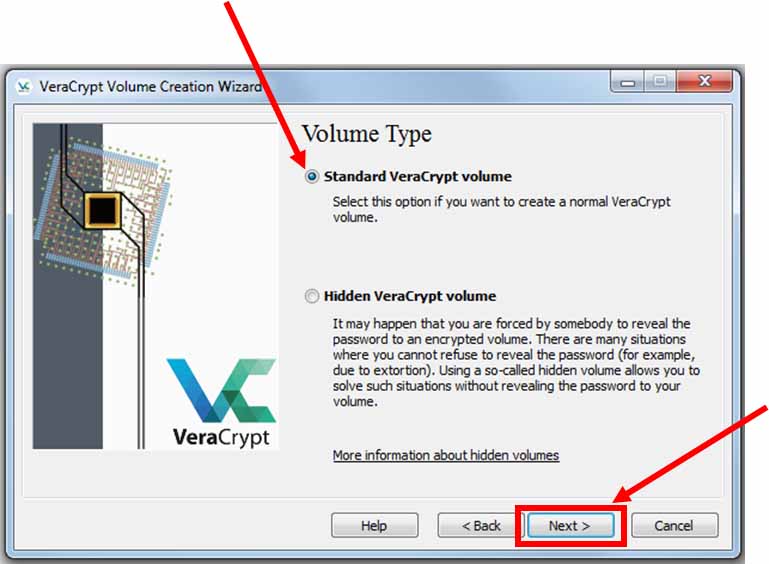
Ensure the “Standard VeraCrypt volume” option is selected and click “Next”
-
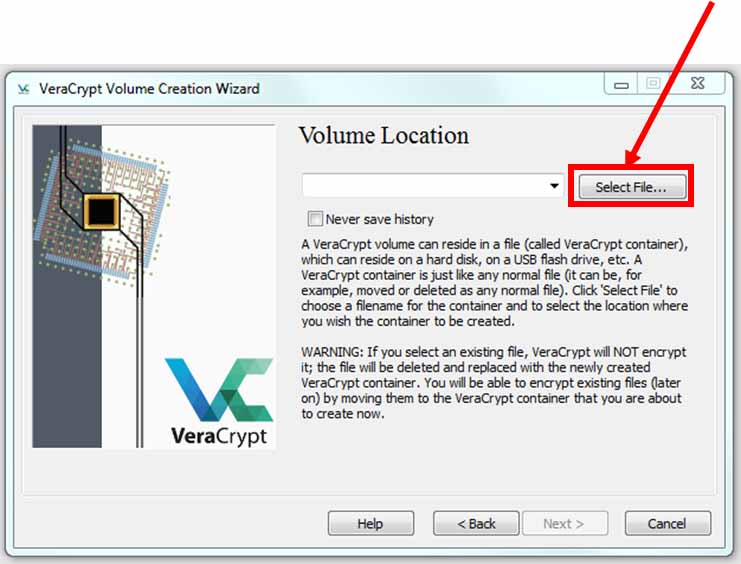
Click “Select File...”
-
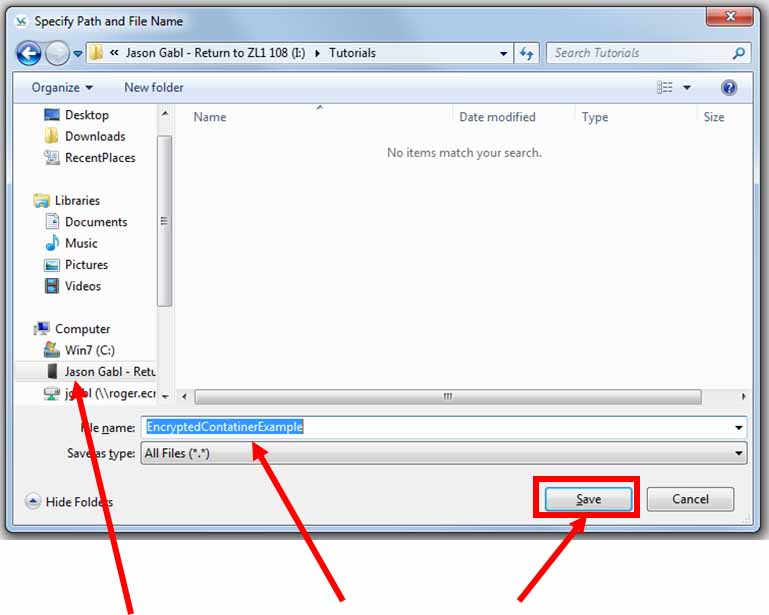
Choose the location where you want the actual encrypted files to be saved (in this case an external hard drive), choose a file name for your container (in this case “EncryptedContatinerExample”), and click “Save”
-
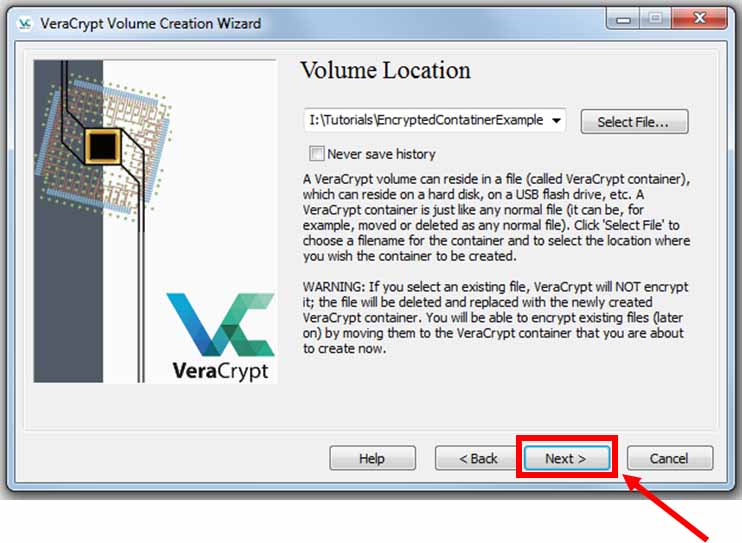
Click “Next”
-
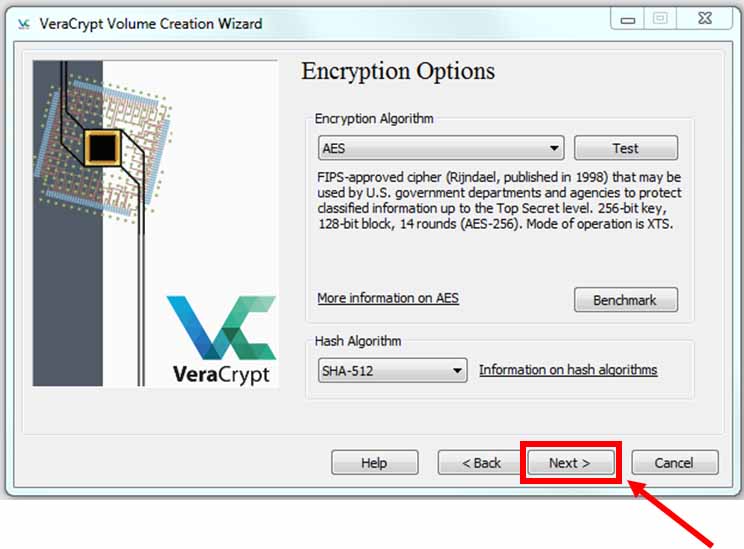
The standard options shown below are the preferred ones, so click “Next”
-
Choose the volume size that you would like to create keeping in mind what type of files you will be storing/processing (in this case 1GB, solely for illustrative purposes)
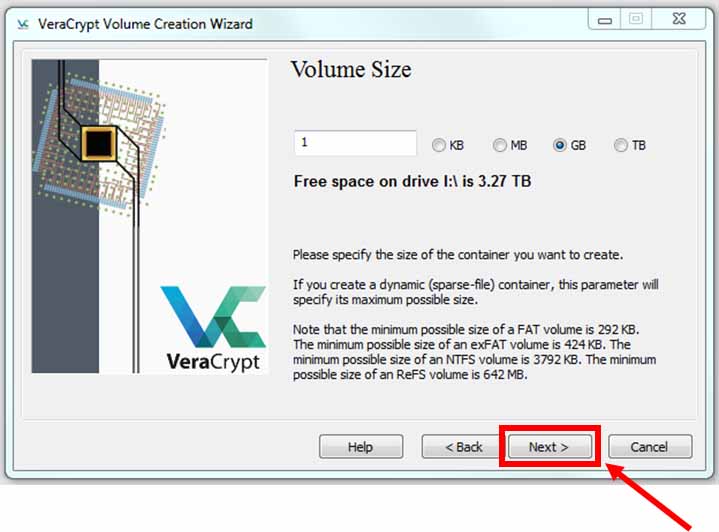
Large volumes (>1TB or so) can take a long time to create. If you will need to process video, nothing smaller than 100GB is recommended based on prior experience. Consider that if you run out of space on one volume, you will then have to either create a larger volume and migrate your encrypted files between containers or have a second volume and store things across two volumes. You might be prompted (depending on the volume size you create) if you want to store large files within your container, enable this option if asked
-
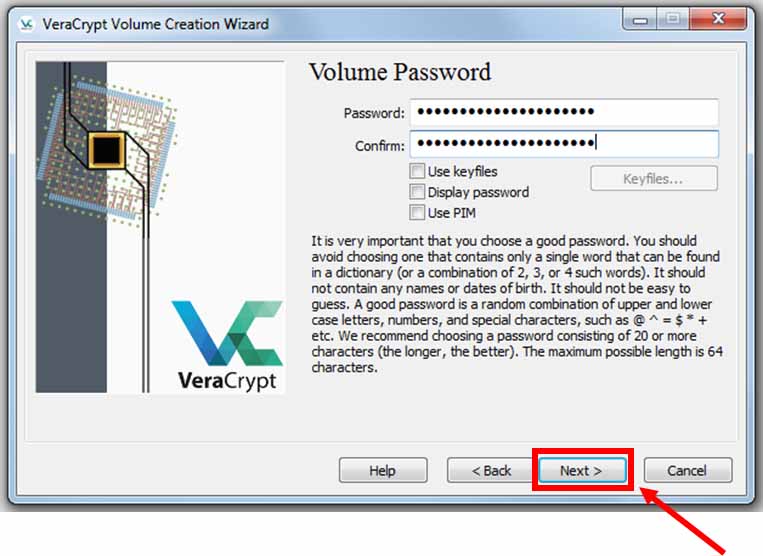
Create a password (the recommendations are shown in the VeraCrypt window, these guidelines may seem extreme, however, your encryption is only as strong as your password, so adequate length and complexity is a must) and click “Next”
-
You will be prompted to randomly move your mouse, do this until the “Randomness Collected From Mouse Movements” progress bar turns green, and then click “Format”

-
It will take more or less time to actually create the volume depending on the container size and where it is being made (large volumes/non-local destinations will take the longest), but once the volume has been created, click “OK”

-
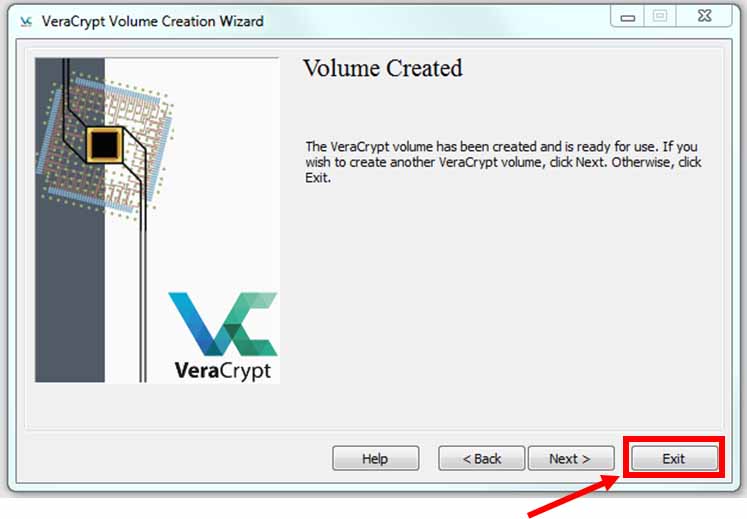
You are done creating your encrypted file container, Click “Exit”
Usage
-
To use your new file container, open VeraCrypt, and click “Select File…”
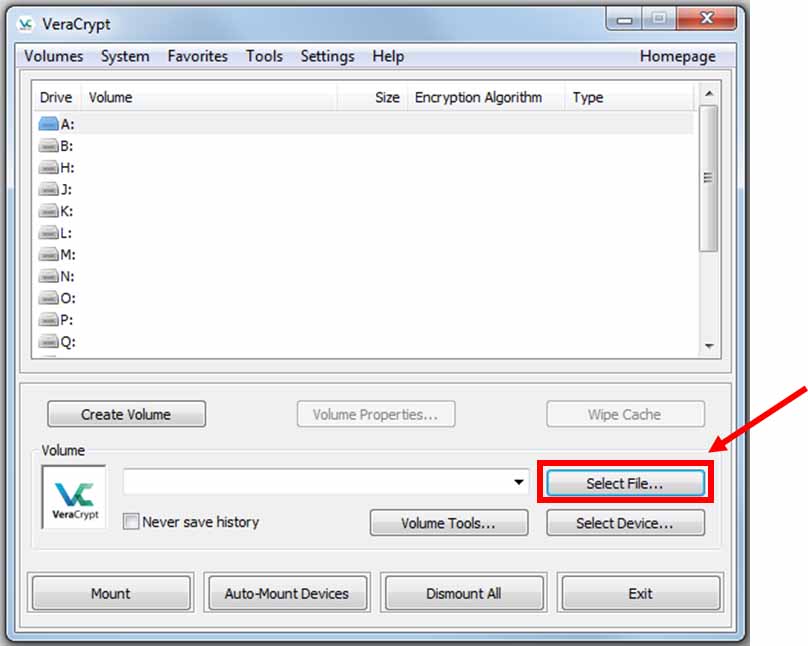
-
Find the volume you created (in this case “EncryptedContatinerExample”) and click “Open”
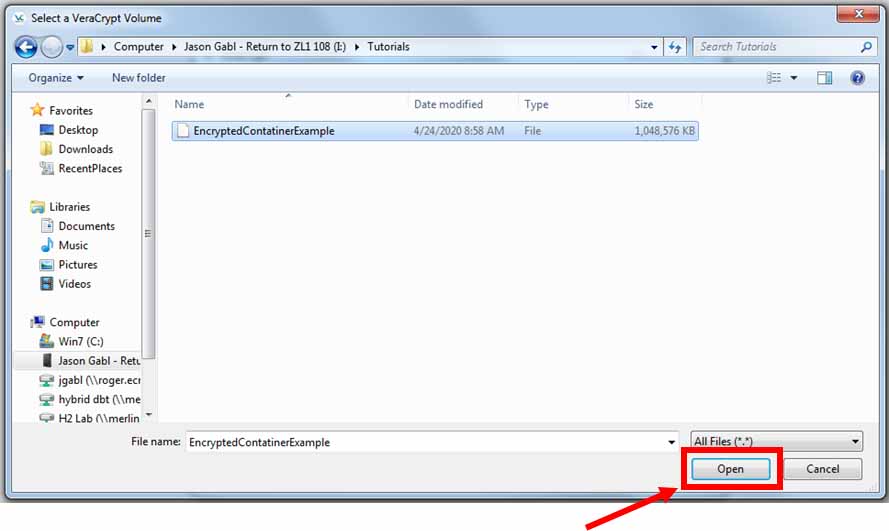
-
Select what you want to call the drive once it is mounted (this is somewhat arbitrary, but you may need to stay consistent if you have data reduction codes or something that references a file location within the encrypted drive), and click “Mount”
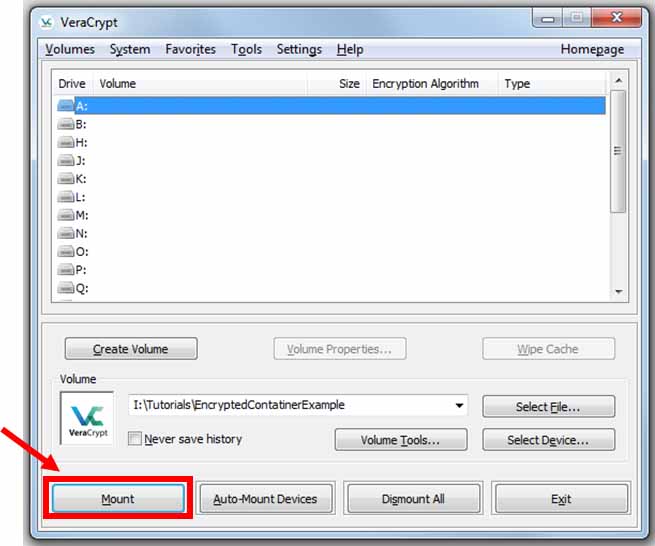
-
Enter your password and click “OK”
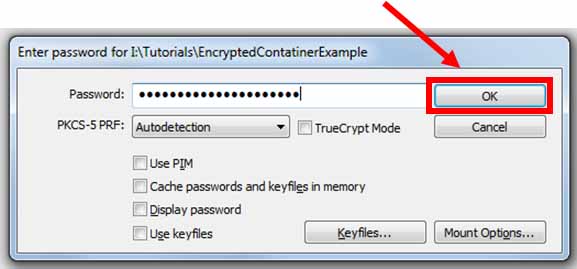
-
The encrypted container is now mounted and ready to be used, you can “X” out of the VeraCrypt GUI and it will run in the background
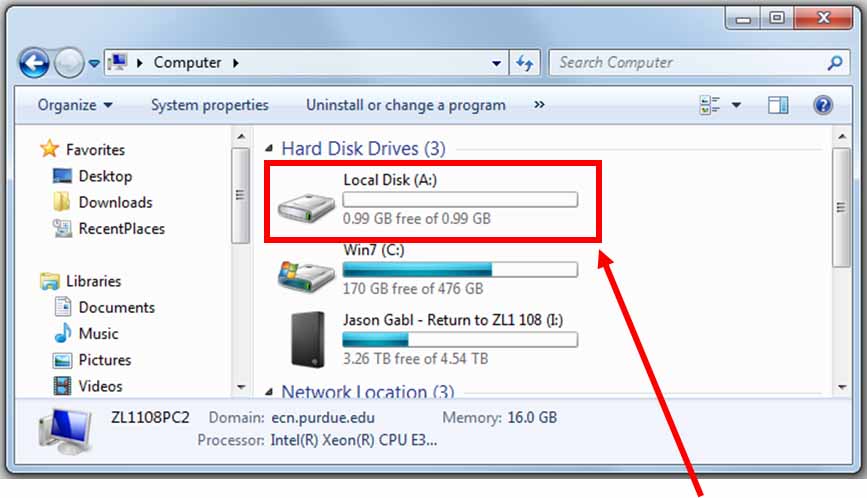
The encrypted container mounts as an extra disk drive on your computer, save and delete files as you would with any other drive (ALWAYS save restricted data directly to this drive to keep it encrypted)
-
When you are done with your encrypted files, close everything and click “Dismount” in the VeraCrypt GUI

NOTE:
BACKUP your files/folders regularly! You can do this by copying the VeraCrypt file (your created volume) or just copy individual critical files within your volume when you have the volume mounted.
Contact Information
Address:
Young Hall, 5th floor
Room 548
155 South Grant Street
West Lafayette, IN 47907
Email: rsec@purdue.edu
Phone: (765) 494-1642
- Guidance Documents
- Foreign National Process for DOE
- Cybersecurity Tips and Resources During the COVID-19 Response
- SPS and OTC NDA Process with Export Controls (login required)
- Connecting to Weber (login required)
- Weber Endpoint Informational (login required)
- Social Distancing Guidance for Controlled Projects (login required)
- Teleconferencing Guidance for Controlled Projects (login required)
- Prior Approvals for Routine International Shipments (login required)
- Managing Export Control Risks in Contract Negotiations (login required)
- Non-Disclosure Agreement Process for Strategic Partners with Master NDAs (login required)
- Covered Information System Baseline Standard (login required)
- Marking Research Documents/Presentations and Ensuring Appropriate Access
- VeraCrypt Installation and Use
- Cybersecurity Tips and Resources for Academic Researchers
- Controlled Thesis Submission Process
- EAR Temporary License Exceptions
- Export Classification
- Engineering Example List
- Restricted Biological Agents
- International Shipping Documentation
- DoD SAFE Outage Guidance
- Fundamental Research and Government Contracts: Implications for Export Controls
- Cuban Travel

