Phishing is a form of Social Engineering attack that targets the user to reveal sensitive information like login credentials, Bank details, credit card numbers, etc. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link, which can lead to the installation of malware, freezing of the system (as part of a ransomware attack), or revealing of sensitive information.

Email Phishing:
Among many types of Phishing, the most common one is Email phishing. Where the attacker sends a pseudo legitimate mail which will try to fool the user into giving personal information like login information and credit card numbers.
Spear Phishing:
Spear Phishing is more of a targeted type of phishing where the attacker targets a particular person/group. It is a potent variant of phishing, a malicious tactic which uses emails, social media, instant messaging, and other platforms to get users to divulge personal information or perform actions that cause network compromise, data loss, or financial loss
How to Identify Them?
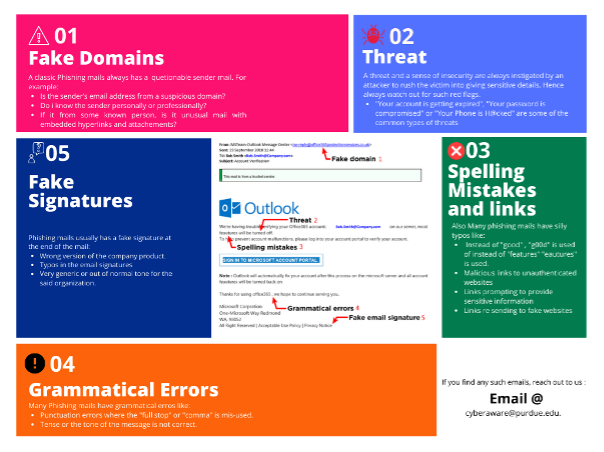
How to stay safe?
- Strong Password and 2FA
It is a best practice to have strong passwords which is of:
- Minimum of 8-40 character length
- Has both uppercase and lowercase character with one special character and digits
Also, it is advisable to Two Factor Authentication along with strong password where along with username and password verification, an OTP is sent to the registered mobile number.
- Antivirus:
One best advice to avoid phishing attack is to think twice before giving sensitive information or clicking the links that are sent to us. It is also of best practice to have some good Antivirus software and Firewalls installed in our system to identify such malicious programs that gets installed in case we click some malicious links. Antivirus software will quarantine such malicious software from getting installed in our systems.